🖼️Overview
This is a preview of our protocol. All documentation here is still work in progress.
The Legitimate Protocol
The Legitimate Protocol is an secure decentralized framework designed to keep physical products in-sync with unique digital identities, specifically from an ownership and provenance perspective. When integrated into the Legitimate Protocol, a product is capable of becoming a phygital (physical + digital) product.
NFC Tags operating on the Legitimate protocol can be by used by customers to verify the authenticity and ownership of physical goods through Legitimate's infrastructure and decentralized smart contracts.
How it works
NFC tags powered by the Legitimate protocol have a few key features:
Unique Digital Identity
A decentralized digital ID that satisfies most provenance and traceability protocols, designed to track products through their entire lifecycle. Owners can scan the NFC tag to claim ownership of a product.
Secure
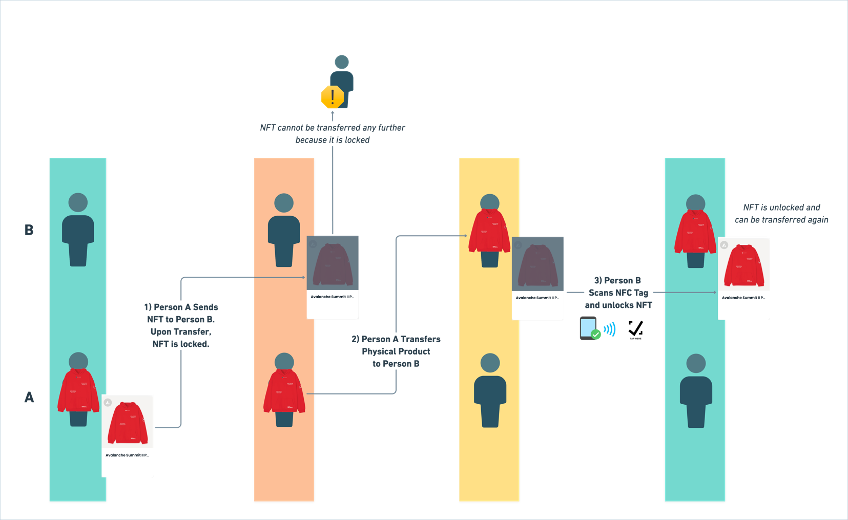
A digital ID can be transferred from one owner to another to record any change in ownership. Our Locking Mechanism (defined below) is a secure escrow implementation that ensures the digital ID and the physical product belong to the same person.
A digital ID is “locked” and cannot be unlocked or transferred until the NFC tag on the physical product is scanned by the new owner to unlock.
Extensible
Third party developers can build on top of this “locked” digital ID state to provide exclusive gated content, access, and more.
Last updated
Was this helpful?


